If your company has experienced security issues, you may be wondering where you went wrong? You’ll be surprised to know that when it comes to protecting your infrastructure, there’s more to it than just the physical location of your servers and the software security you utilize.
What Can We Learn From Sony?
In 2011 Sony was the subject of a security breach when their PSN network was hacked and again in 2014 when their Sony Pictures division was hacked. As previously mentioned, the Hollywood myth surrounding hackers, that your data is easily available to hackers, isn’t necessarily accurate. The truth is, it’s only as accessible as you make it.
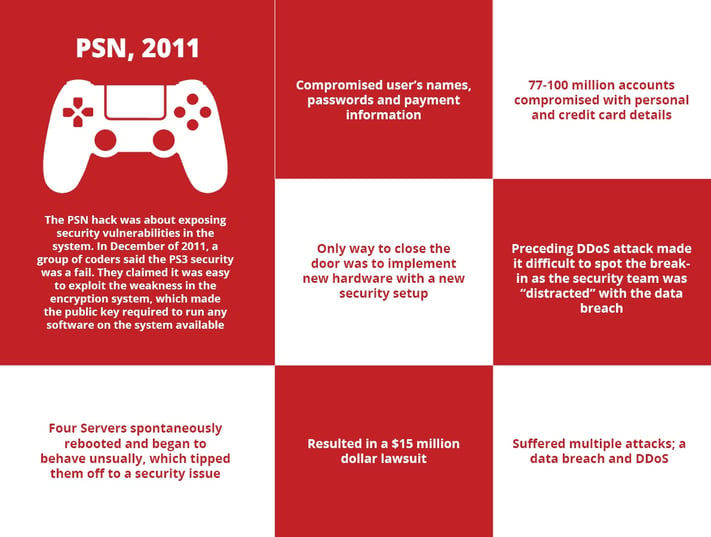
PlayStation Network Hack:
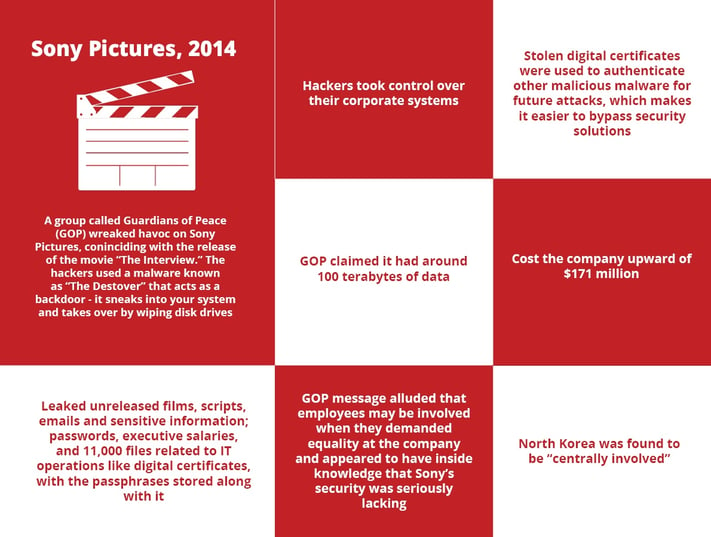
Sony Pictures Hack:
The Biggest Security Threat
According to Fortune, Sony’s organizational structure prevented them from effectively implementing new measures to protect themselves after the 2011 attack, as many companies that operate in different divisions don’t communicate between each other. However, communication can also be a problem for smaller companies and it’s important to collaborate and share within your entire organization. This not only strengthens your company but can also decrease and/or weaken security breaches.
One of the issues that arose during the Sony hack to make note of, is it was revealed they were “not operating with adequate protection against phishing attacks, remote-access Trojans, password management policies, proper use of encryption, data storage, and backups.”
In 2016 IBM reported that 60% of all attacks suffered by their customers were carried out internally. Aside from the issue of malicious employees intentionally leaking information, others are vulnerable to phishing attacks which target your employees in the form of email attachments or compromised websites. These types of attacks are far more common and relevant to all businesses, as opposed to a sophisticated attack by hackers.
What this means is that whether you’re dealing with disgruntled, careless or uninformed employees, people are still the weakest link.
How to Protect Your Organization?
- Easy to collaborate and share among employees
- Remote-access for telecommuting
- High-level software security
- Backup with encryption
- Replication to leverage disaster recovery solutions
Mitigate risks with employees:
- Your employees likely have knowledge and access to networks and accounts. Make sure you have protocols in place for current employees, like logging activity or immediately removing privileges for terminated employees.
- Train your employees in best security practices; password protection, unauthorized visits to websites and suspicious emails or attachments. Provide your employees with the resources they need to protect themselves and your organization.
With how fast our online world is growing, it’s impossible to completely prevent security breaches, but we also don’t want to make it easy for our data to be stolen. There are so many resources and services available to decrease the likelihood of disaster, like utilizing the cloud, hosting your infrastructure off-site at a data centre and educating your employees on best security practices.
-1.png?width=1092&height=792&name=logo%20(1092x792)-1.png)
%20copy(black%20letters).png?width=1092&height=792&name=logo%20(1092x792)%20copy(black%20letters).png)




.png?width=100&height=91&name=white%20logo%20(100x91).png)